Today all we hear is that end-to-end encryption is the way to go and it is very secure. And That’s all we know, and ever since WhatsApp, Signal among other social communication platforms announced their implementation of end-to-end encryption, everyone has embraced use of these platforms.
We want to tell you more about end-to-end encryption and why you need to have it in your communications. We shall keep this article simple for everyone to understand.
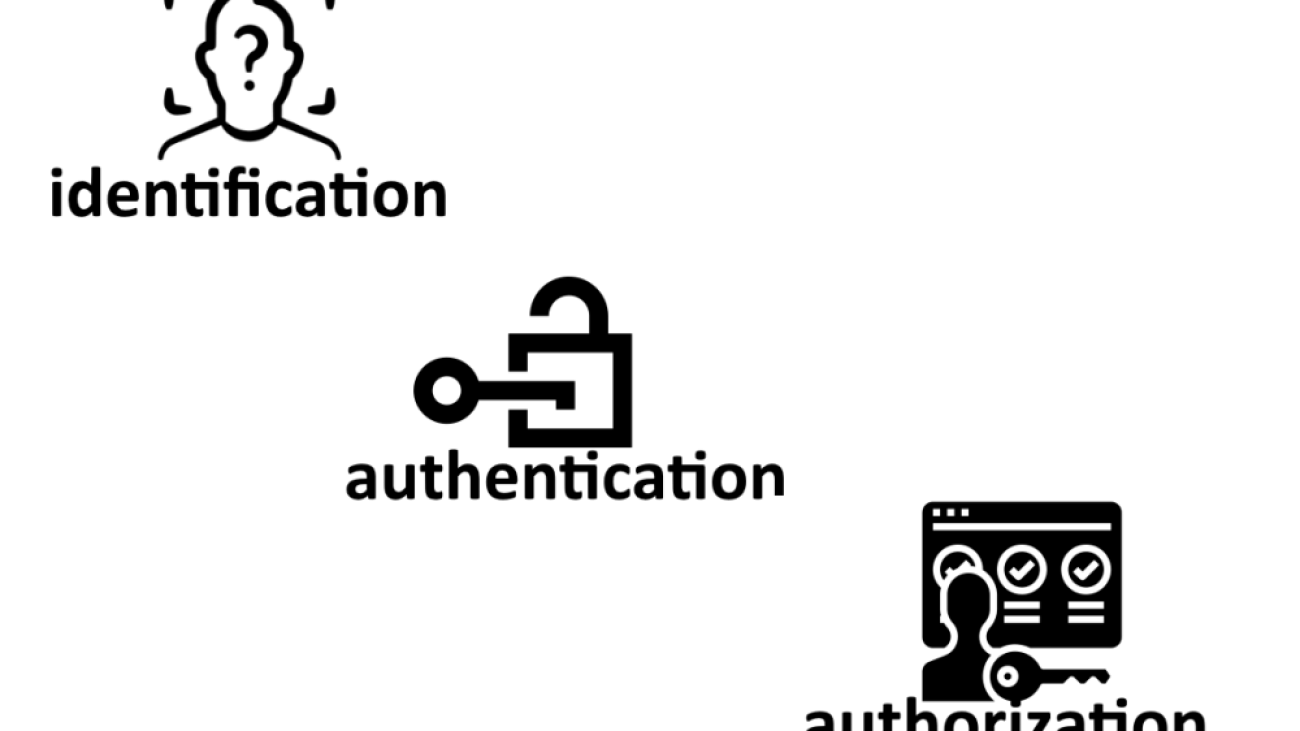
What is encryption? This is a process that encodes a message or file so that it can be only be read by certain people.
This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information
What is end-to-end encryption? This is the act of applying encryption to messages on one device such that only the device to which it is sent can decrypt it. The message travels all the way from the sender to the recipient in encrypted form.
Why end-to-end encryption?
- The biggest reason why we need to communicate via platforms that offer end-to-end encryption is the security of our communication while it is in transit from you the sender to the recipient.
“It is as if when you mailed a letter you put it in a box that was physically impossible to open — immune to any sledgehammer, saw, lockpick, and so forth — except by the addressee. End-to-end encryption ensures the privacy of your communication.” - The second reason could be the fact that since no one is able to intercept your message, therefore no one can make changes to your message until it reaches the recipient of the message. This promotes integrity.
What more can you do? Having all your communication through end-to-end encrypted channels might make you feel secure, although there is much more you can do to further protect your communication.
Make sure to keep your communication device safe because if someone gets hold of your device, they can read all your messages and therefore encryption wont help you.
Keep your device safe by: Using an access lock (password/PIN/pattern) and set your device to automatically lock in a few seconds, Use Genuine software on your devices
Secondly, even if you protect your device – you might not be certain about the device of your recipient, so in this case, spread the word to make sure your devices are all safe
You can also read more on this here https://usa.kaspersky.com/blog/what-is-end-to-end-encryption/23288/