We all have been identified, authenticated and authorized almost everyday of our online life.
What we do not know most of the time is where each of this comes in while accessing our online platforms and we end up confusing the 3 words often using the terms identification or authorization when, in fact, they are talking about authentication.
But as long as we are able to understand what we are talking about, it has not mattered to us to get the meanings of these 3 words.
It is always better to know the meaning of the words you use, though, and sooner or later, you will run into a geek who will drive you crazy with clarifications, whether it’s authorization versus authentication, fewer or less, which or that, and so on & to be honest, you could even catch an attitude!
So what do these 3 words actually mean?
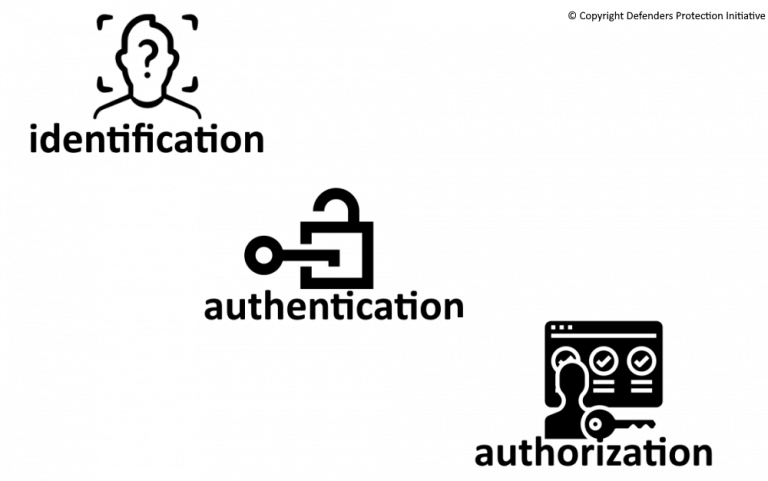
- Identification occurs when a subject claims an identity (such as with a username)
- Authentication occurs when a subject proves their identity such as with a password (for example, by comparing the password entered with the password stored in the database)
- Authorization techniques can grant or block access to objects based on their proven. This is the function of specifying access rights/privileges to resources.”
🙂
So, now you know in what ways identification is different from authentication and authorization. One more important point: Authentication is perhaps the key process in terms of the security of your account. If you are using a weak password for authentication, your account could easily be hijacked. Therefore:
- Create strong and unique passwords for all of your accounts.
- If you have trouble remembering your passwords, a password manager has your back. It can help with generating passwords, too.
- Activate two-factor authentication, with one-time verification codes in text messages or an authenticator application, for every service that supports it. Otherwise, some anonymous raccoon that got its paws on your password will be able to read your secret correspondence or do something even nastier.
The 3 words are so easy to confused and people always get mixed up using them. Hope this article has made it clearer now!