More children and teenagers are actively engaging with the internet, and this trend is expected to persist. However, the online environment hasn’t always been tailored to cater to the needs of minors. Therefore, it is crucial to prioritise their safety. In honour of Safer Internet Month, here are some essential tips and tools parents, educators, and even the young netizens can use to guarantee online safety.
Data Privacy and Protection: Essential Insights for NPOs.
Like other organisations/companies, Non-Profit Organisations (NPOs) collect and utilise data from their program participants, partners or donors. It is therefore imperative that they prioritize data privacy and protection.
Data privacy and protection essentially entail safeguarding sensitive personally identifiable information, covering data collection, storage, and organizational use. Data collected by NPOs may include details such as names, addresses, emails, and financial information.
Here are key insights for NPOs as they navigate the landscape of data privacy and protection.
Why Data Privacy and Protection?
Data protection and privacy aren’t just checkboxes for NPOs; failure to safeguard sensitive information can lead to severe consequences, posing significant risks to organisations.
Loss of Data
Losing valuable data can be detrimental to an NPO’s operations. Whether it’s program participant information, donor records, or financial data, the loss of such information can disrupt essential activities and hinder effective decision-making. Additionally, recovering lost data can be a time-consuming and costly process.
Financial Loss
Data breaches can lead to financial losses. NPOs may face financial liabilities associated with rectifying the situation. This could include expenses related to legal actions, regulatory fines, or compensating affected individuals. By implementing robust data protection measures, the risk of financial loss can be minimised and resources can be allocated to their core mission.
Damage to Reputation
NPOs and civil society organizations in general rely heavily on the trust and support of their stakeholders, including donors, partners, and the civil society at large. A data breach or mishandling of sensitive information can severely damage their reputation. Negative publicity, loss of trust, and public scrutiny can have long-term consequences.
What to Do: Take Action
Digital Security
One of the primary steps in ensuring data protection is to prioritize digital security—measures to secure all data collected, processed, or stored electronically. This includes implementing robust firewalls, encryption techniques, and access controls to prevent unauthorized access or damage to sensitive information. Regularly updating security software and conducting vulnerability assessments can help identify and address any potential vulnerabilities in the organization’s systems. Additionally, establishing strong internal policies and educating staff about cybersecurity best practices can significantly enhance data protection.
Transparency
It is crucial to provide data subjects with enough information to make informed decisions about the data collected from them to obtain informed consent. This includes being transparent about the purpose of data collection, how it will be used, and whether it will be shared with any third parties. This can be achieved through clear and concise privacy policies, consent forms, and opt-in mechanisms.
Compliance
Compliance with relevant data privacy and protection laws can minimise the risk of legal consequences and demonstrate their commitment to protecting individuals’ privacy.
The Personal Data Protection and Privacy Act 2019, spells out specific regulations on data handling. It may also be helpful for NPOs to familiarise themselves with international laws, such as the General Data Protection Regulation (GDPR), to stay informed about how data may be used by third parties operating under EU jurisdiction. This also ensures that they (NPOs) handle data from the same jurisdiction in a way that aligns with the required standards.
Where To Start: Available Resources
- The Personal Data Protection Office (PDPO) website serves as a comprehensive guide for NGO registration and reporting processes and also offers valuable informative material.
- At DPI, we provide training and capacity building in data privacy and protection specifically tailored for NGOs. Feel free to reach out to us here for assistance.
The Strength of Strategic Coalitions: Showcasing the Impact of the Digital Security Alliance and NPO Coalition on FATF.
The pivotal role played by strategic coalitions in advancing our mission cannot be overstated. This month we highlight key wins of the Digital Security Alliance (DSA) and the NPO Coalition on FATF, shedding light on their contributions to empowering Human Rights Defenders (HRDs) and cultivating supportive ecosystems.
Digital Security Alliance (DSA)
Digital Security Clinics:
Through our Digital Security Clinics, we have significantly extended our impact in fortifying the cybersecurity resilience of HRDs. This month’s focus was on empowering grassroots HRDs and CBOs, which are most burdened with emerging digital challenges such as limited access due to slow or no internet connectivity, data loss, and the absence of enabling ICT hardware and infrastructure, such as cell towers and computers.

The Digital Security Clinics successfully fortified the digital security capacity of civil society organizations (CSOs) in the Eastern subregion, including the Pallisa Civil Society Organization Network (PACONET), Public Affairs Center of Uganda (PACUganda), Soroti, the Kapchorwa Civil Society Organizations Alliance, and the Joshua’s Cheptegei Development Foundation.

DSA served as the official digital security partner for the 5th edition of the Human Rights Convention hosted by Chapter Four Uganda and the 5th Annual Women’s Week hosted by Uganda Women’s Network (UWONET). These workshops addressed multifaceted issues, including limited access, insufficient digital literacy, and socio-cultural barriers discouraging women’s engagement with ICT.
NPO Coalition on FATF
Global NPO Consultation on Recommendation 8
The Global NPO Coalition on FATF played a pivotal role in the success of the “Risk and Consequence: The Future of FATF Recommendation 8 for Financial Integrity and Civil Society” conference. This convening brought together policymakers, standard setters, financial institutions, nonprofit organizations (NPOs), multilateral organisations, academics, and think tanks, all of whom contributed their input to the revision of the FATF Recommendation 8.
Furthermore, the Coalition submitted recommendations to the FATF Public Consultation on revisions to Recommendation 8 and its Interpretive Note. The approved revised standard clarifies the application of the risk-based approach, acknowledges sectoral self-regulation measures, and explicitly states that NPOs should not be considered obliged entities.
As we reflect on the achievements of the Digital Security Alliance and NPO Coalition on FATF, we are inspired to continue fostering alliances, enhancing outreach, and creating lasting impacts on the front lines of advocacy. The journey toward safeguarding human rights defenders remains a collective endeavor, and we look forward to the shared progress that lies ahead.
Simple Digital Security Measures YOU Should Implement
As we end #CyberSecurityAwareness month, you have most likely consumed a wealth of information, including dos and don’ts, warnings, and cautionary tales. We understand that some of this content might appear complex or daunting to grasp. So here are a few straightforward yet highly impactful digital security measures that you can implement today to stay one step ahead in the realm of cybersecurity.
Securing Your Messages and Calls
While most messaging platforms like Signal, WhatsApp, and Telegram offer end-to-end encryption for messages and calls, you can go a step further in fortifying the security of your communications by using Face ID or Finger Print Lock as an additional layer of protection from unauthorized access to your messages.
However, it is important to utilize this feature alongside a pattern unlock or PIN because once biometric data is compromised, it cannot be replaced.
For Apple users, it’s important to limit the scope of your messages and, if necessary, disable messages in iCloud for enhanced privacy and security. By doing this, you can restrict the synchronization of your messages to a single device, minimizing the risk of unauthorized access or data leaks.
Using VPN for Secure Browsing
In Uganda, many of us primarily associate Virtual Private Networks (VPNs) with bypassing blocked social media platforms like Facebook. However, the utility of VPNs extends far beyond this. They add a crucial layer of security by encrypting your internet connection and shielding your online activities from prying eyes whether you are engaged in tasks within your Google Suite or conducting online banking transactions
Browsers like Opera and Tor come with a built-in VPN, eliminating the need to constantly toggle it on and off.
Password and Pass-Keys Generators
Managing strong and unique passwords for all your online accounts can be a daunting task. Luckily, both the Play and App stores offer a password generator that can generate and save passwords for your multiple online accounts. However, exercise caution and use this feature on private computers only. Unauthorized access to your Google Account or Apple ID could lead to breaches of your other accounts.
Software Updates
Downloading and installing software updates for your devices and the applications used on them is one of the simplest methods to maintain optimal digital security. These updates enable tech companies to fix any bugs and vulnerabilities in their products that could be exploited by hackers or malware. Don’t ignore that software update notification on your computer any longer!
By implementing these simple digital security measures, you can significantly enhance your online safety and protect your valuable information from potential threats. Remember to remain vigilant and enjoy secure browsing.
Harnessing the Potential of Collaboration and Partnerships for Social Impact

The significance of partnerships and collaborative efforts in advancing the goals and activities of civil society has become more evident than ever before. This month, we take a moment to reflect on the profound impact of collaboration and partnership in advancing our mandate.
Fostering Knowledge Exchange
In collaboration with the Civic Advisory Hub and the NPO Coalition on FATF – East and Southern Africa Chapter, we took a significant step forward in advocacy efforts for the adoption of a risk-based approach to the monitoring and legislation of NPOs in the context of countering terrorism financing.
During a successful webinar titled “Understanding NPO Risk Assessment on Terrorism Financing,” NPO leaders from the region shared their experiences, lessons learned, and criteria for NPO risk assessment working groups. Together, we explored the critical role that NGOs play in these assessments and discussed the essential qualities required for effective participation.
Empowering Communities through Digital Security: Our #RoadToFIFAfrica Journey
We embarked on an exhilarating regional campaign known as #RoadToFIFAfrica, spanning from Kampala to Nairobi, Mombasa, and culminating in Dar es Salaam. Throughout this journey, we actively connected with local communities, students, CBOs, and NGOs to address the vital topic of digital security. Our mission was clear: to equip individuals and organizations with essential digital security skills, provide them with valuable tools and knowledge, and empower them to navigate the digital world safely and confidently.
Championing Internet Freedom at FIFAfrica23
With support from CIPESA Uganda and in collaboration with Encrypt Uganda, and HRD Andrew Gole, our commitment to digital security extended to Africa’s largest gathering on Internet freedom, the Forum for Internet Freedom in Africa (#FIFAfrica23). Through the Digital Security Alliance, we extended digital security support to some of the brightest minds in Africa and worldwide, fueling their tireless efforts to safeguard internet freedom both on the continent and globally.
Multi-Sector Support and Collaboration
In addition to these dynamic initiatives, we maintain active engagement with key government ministries and agencies including the Financial Intelligence Authority (FIA) and the National Information Technology Authority (NITA-U) among others.
Our objective is to provide valuable sector insights and foster collaboration to create an enabling and supportive environment for Human Rights Defenders(HRDs) and activists. Through our regional “Talk To Your Regulator” sessions, we aim to strike a delicate balance between fostering compliance and preventing excessive regulation. We achieve this by creating awareness among NGOs about their legal compliance requirements and responsibilities while also engaging regulators on the unintended consequences that overly restrictive regulations can have on the sector. Our ultimate goal is to ensure that members of civil society can effectively fulfill their missions. This month’s engagement took place in Hoima, marking another milestone in this ongoing effort.
Suffice it to say that our journey this month underscores the power of collaboration and partnerships in driving transformative change and fostering social impact. Here’s to more partnerships and collaborations ahead.
Digital Security Conference #DigiSecCon21
Defenders Protection Initiative will bring together actors from civil society, the private sector, business leaders, government, academicians, technologists, activists, journalists and subject matter experts to tackle pressing issues at the intersection of human rights, technology and security.
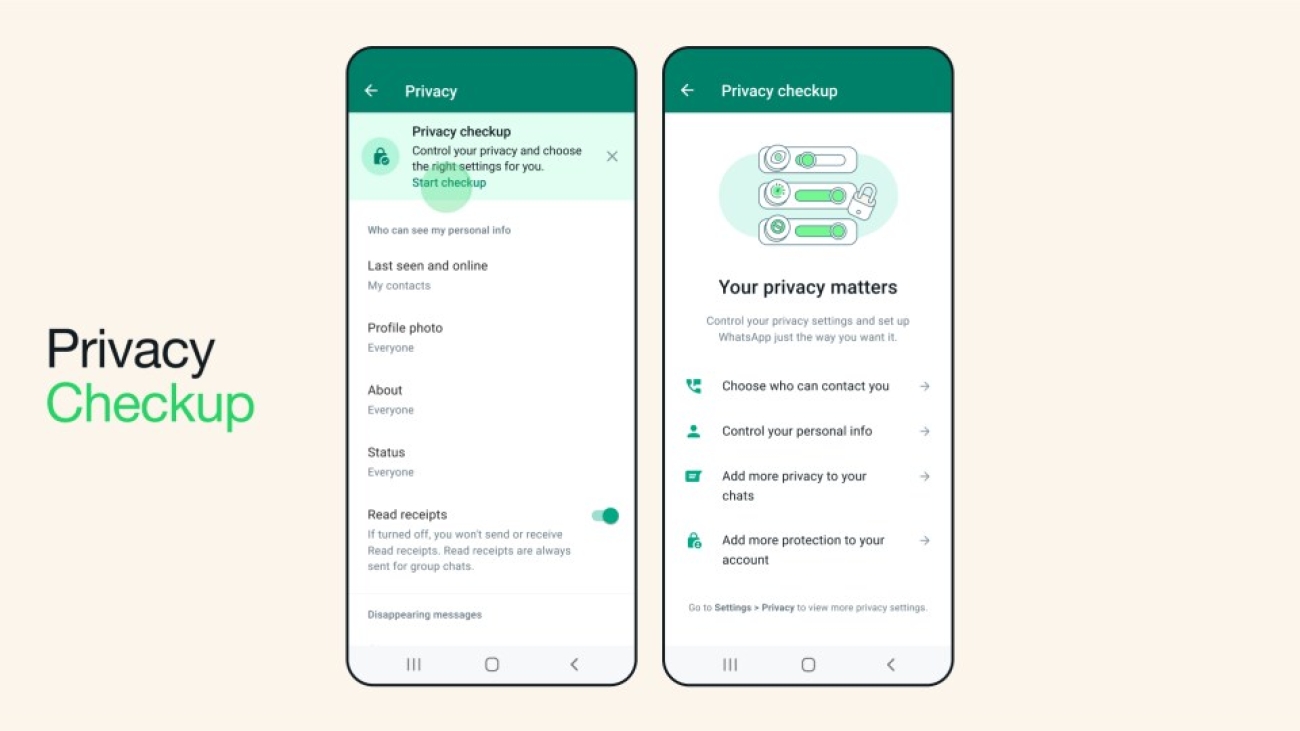
WhatsApp 2FA: Secure Yourself From This Simple Hack
Imagine someone has taken over your account, what would happen to you and the people who contact you on WhatsApp?
Just as it is easy to fresh install of WhatsApp for your new phone is also how easy an attacker would gain access to your WhatsApp and possibly start a conversation with your friends claiming it is you.
Most times, the direct risk is not to you if you’re attacked, but to your contacts. They can expect to receive requests for data or even emergency funds. This is social engineering at its best. We would trust an end-to-end encrypted platform, a message from a trusted friend and so are coded to have our guards down and rather feel pity in these circumstances.

The repercussions of this happening are beyond imagination. This can even further spread to more of your contacts having there WhatsApp accounts taken over.
With the account taken over, the attackers could then message contacts in the groups you are in as if from the account holder (you), as well as any other contacts whose WhatsApp messages were received after the take over. No legacy data is compromised. The target device remains untouched. WhatsApp has simply been ghosted onto an illegitimate device.
It is surprising how many people have not yet enabled the Two-step verification PIN in WhatsApp—almost everyone we have asked has yet to set it up. If you’re the same, then please take that minute and set it up now.
The Question now is, How do we prevent this from happening to you for the first time or again?
WhatsApp introduced a feature where you can set a PIN of your own choice and even an email address just in case you forget your PIN. The PIN is your own verification to confirm that it is you even after inputting the SMS verification so you do not otherwise have to share your PIN with anyone.
You can find this feature in your WhatsApp setting > Account > Two-step verification: There you will be prompted to enable your PIN and confirm it, then you will also be asked to type in an email address to use to recover your account in case you forget your PIN
End-to-End encryption: What is it, Why you need it, What more you can do
Today all we hear is that end-to-end encryption is the way to go and it is very secure. And That’s all we know, and ever since WhatsApp, Signal among other social communication platforms announced their implementation of end-to-end encryption, everyone has embraced use of these platforms.
We want to tell you more about end-to-end encryption and why you need to have it in your communications. We shall keep this article simple for everyone to understand.
What is encryption? This is a process that encodes a message or file so that it can be only be read by certain people.
This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information
What is end-to-end encryption? This is the act of applying encryption to messages on one device such that only the device to which it is sent can decrypt it. The message travels all the way from the sender to the recipient in encrypted form.
Why end-to-end encryption?
- The biggest reason why we need to communicate via platforms that offer end-to-end encryption is the security of our communication while it is in transit from you the sender to the recipient.
“It is as if when you mailed a letter you put it in a box that was physically impossible to open — immune to any sledgehammer, saw, lockpick, and so forth — except by the addressee. End-to-end encryption ensures the privacy of your communication.” - The second reason could be the fact that since no one is able to intercept your message, therefore no one can make changes to your message until it reaches the recipient of the message. This promotes integrity.
What more can you do? Having all your communication through end-to-end encrypted channels might make you feel secure, although there is much more you can do to further protect your communication.
Make sure to keep your communication device safe because if someone gets hold of your device, they can read all your messages and therefore encryption wont help you.
Keep your device safe by: Using an access lock (password/PIN/pattern) and set your device to automatically lock in a few seconds, Use Genuine software on your devices
Secondly, even if you protect your device – you might not be certain about the device of your recipient, so in this case, spread the word to make sure your devices are all safe
You can also read more on this here https://usa.kaspersky.com/blog/what-is-end-to-end-encryption/23288/