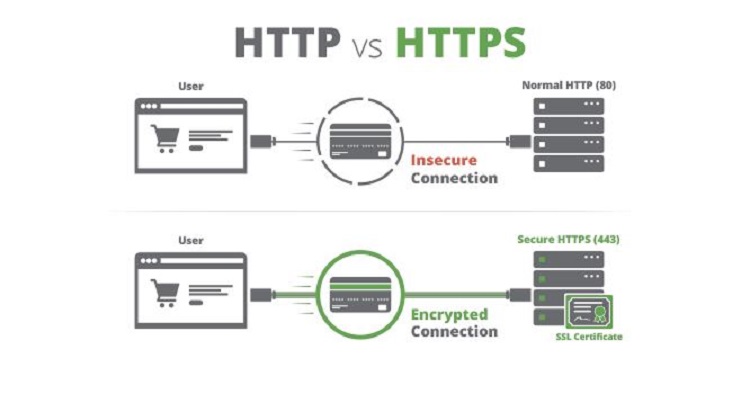
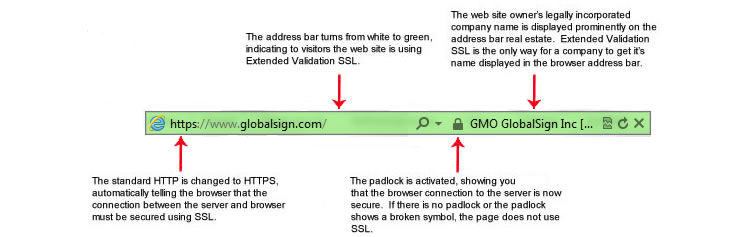
Often when you talk of securing our web hosting, our minds are led to “Which host is can not be hacked?” But it is beyond that, some time we need to secure ourselves beyond just that. Things like, who signed up for the server? Which email was used? What name was used to register the domain?
Just before we look outside and start blaming web hosting service providers, we have to ensure that we personally take these tips to safeguard our service.
#TIP 1. Since this is your service so first thing is to have all credentials pointing towards you. Credentials such as usernames, emails that are used to identify you to your web hosting provider don’t have to belong to a third party but rather you. This makes it easy to recover your account easily.
#TIP 2. Enforce password complexity and 2 step verification. To make sure login is secure, you need to have 2FA enable and a strong password. This protects your account from being easily breached by adversaries.
#TIP 3. Avoid using insecure/unsupported third party apps. Web hosting service providers tend to avail you with a multitude of app choices to use for your services, from building your website, to accessing emails, to manipulating your databases. Some of these apps tend to be obsolete or insecure to use in the evolving technology. Therefore you need to look out on more secure applications.
#TIP 4. Update all apps or software used on your web host reguralrly, after making a good choice of what to use, make sure to update this tools regularly. Updates are a way to secure yourself with a fix of identified vulnerabilities or simply to keep abreast with new technology that has been added to a tool.
#TIP 5. Use the most secure web hosting you can find. No matter the content you are hosting or the services to expect from a hosting provider, Always lookout for services that are ideal in the present digital age. We have put together a list of tips to consider when choosing your web hosting provider just below.
Here are a few tips to consider to make a choice of a good hosting provider.
#TIP 1. Ensure the server has a backup policy. Backups no longer just apply to information in your computer but also you need to know that there is another option for your online information in case anything happens. You can control many aspects of backing up your computer data, but for websites, it can often depend on your hosting provider. Good enough, most web hosting providers do offer free backups, but these are variations on this theme. For example, some may require you to perform the backup procedure manually, while others may do it automatically and require you to contact their support team if you should need data restoration services. Ideally, look for a web hosting provider that carries out periodical automated backups and allows you to restore from them at any time on your own.
#TIP 2. Look out for servers with an automated Malware or Antivirus Scanning. Just as you may have an antivirus program on your computer which you are fully in control of. For websites, you depend on the hosting service provider to do this for you. It’s important to at least know they’re doing this and what level of information they can provide to you on potential problems. Some web hosts offer these services and you are able to see their reports and fixes or recommendation. But the very least you need to consider is to be able to restore your site from a previous version that wasn’t infected.
#TIP 3. Consider servers with Network Monitoring, Firewall and DDoS prevention systems. As websites are hosted in massive data centers, much of the controls here are automated. Make a choice on hosts having control and monitoring tools in place that keep an eye out for suspicious traffic or incidences. Firewalls are always our first line of defense from attacks from outside our systems and you need to make sure you have that wherever you are hosting your website. Whereas, Distributed Denial of Service (DDoS) attacks can be a big blow as attacker will want to flood your website with so much traffic to take it down completely from the site server.
These are often mitigated by using a good Contend Delivery Network (CDN) such as Cloudflare or website firewall such as Sucuri. Good enough, some hosting providers include this in their bundles, so look out for them!
#TIP 4. Secure File Transfer Protocol (SFTP). In circumstances where large files have to be uploaded to the website, it is more efficient to use FTP to do this, now there is SFTP which is the secure version of FTP and helps keep your data safe during transfer. While most popular web hosts offer FTP services, a handful of them only seem to offer SFTP so those handful are the ones you should look up to. Unless you do not use FTP or you don’t think of using it, you could skip this tip but we guarantee it is just as important as the rest.
#TIP 5. Spam filtering. You might be well aware of spam or junk. Just as annoying these messages can be is also how they can be a source of DDoS if you are suddenly flooded by such mail. If your host offers spam filtering, then the attack goes through its spam filters first which would be a win for you. Also, keeping spam out will help you save space in your mail folders. Most hosting providers have spam filters available, but some will require manual configuration. We’d suggest using those with automatic spam filters.
Hoping that these tips have been helpful to you, these are just to ensure that you have a smooth web service and you don’t have to be a victim of several hacks on the web. There are endless attacks on websites everyday and the best you can do is to have a secure web hosting service as the internet is an overwhelming place for resources and everyone is trying their best to utilize it in both good and bad ways.