How it Works?
Simplistically speaking, there are three main components in creating a connection;
- The Client – This is the computer that is requesting information.
- The Server – The computer which holds the information being requested by the Client.
- The Connection – The path along which data travels between the client and server.
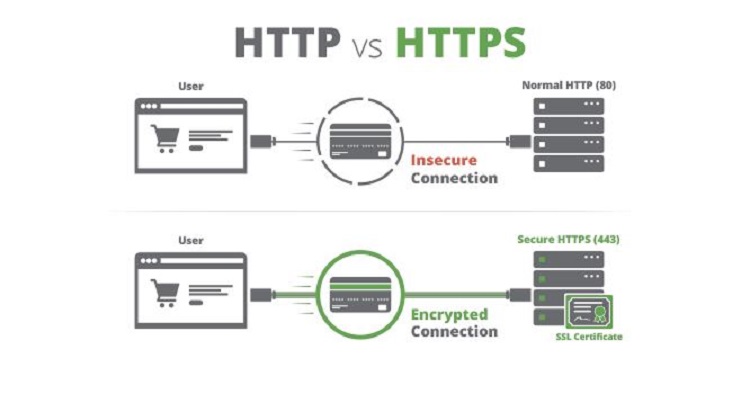
To establish a secure connection with SSL, there are a few more terms you need to be aware of.
- Certificate Signing Request (CSR) – This creates two keys on the server, one private and one public. The two keys work in tandem to help establish the secure connection.
- Certificate Authority (CA) – This is an issuer of SSL certificates. Sort of like a security company that holds a database of trusted websites.
Once a connection is requested, the server will create the CSR. This action then sends data which includes the public key to the CA. The CA then creates a data structure which matches the private key.
The most critical part of the SSL Certificate is that it is digitally signed by the CA. This is vital because browsers only trust SSL Certificates signed by a very specific list of CAs such as VeriSign or DigiCert. The list of CAs are stringently vetted and must comply with security and authentication standards set by the browsers.
Types of SSL Certificates
Although all SSL certificates are designed for the same purpose, not all are equal. Think of it like buying a phone. All phones are basically designed to do the same thing, but there are different companies that manufacture them and produce many different models at varying price points.
To simplify the matters, we break down the SSL Certificate types by level of trust.
1- Domain Validated (DV) Certificate
Among SSL Certificates, the Domain Validated Certificate is the most basic and simply assures users that the site is safe. There is not much detail except for that simple fact and many security organizations do not recommend using Domain Validated Certificates for websites that deal in commercial transactions. The Domain Validated Certificate is the budget smartphone of the SSL world.
2- Organization Validated (OV) Certificate
Organizational Certificates holders are more stringently vetted are by CAs than Domain Validated Certificate holders. In fact, the owners of these certificates are authenticated by dedicated staff who validate them against government-run business registries. OV Certificates contain information about the business holding them and are often used on commercial websites and represent the midrange smartphones of the SSL world.
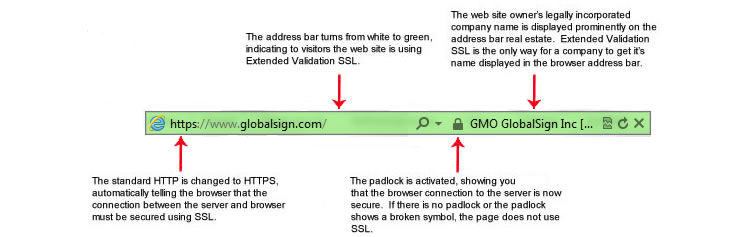
3- Extended Validation (EV) Certificate
Representing the highest level of trust in SSL rankings, EV Certificates are opted for by the best of the best and extremely stringently vetted. By opting to use EV Certificates, these websites are buying deeply into consumer trust. These are the iPhoneX of the SSL world.
The fact that SSL Certification has become so highly recommended today, many fraud websites have also taken to using SSL. After all, there is little difference to the websites, except for the green certification padlock. This is the key reason more reputable organizations are going for SSL Certification that are more highly vetted.
ince any successful SSL connection causes the padlock icon to appear, users are not likely to be aware of whether the website owner has been validated or not. As a result, fraudsters (including phishing websites) have started to use SSL to add perceived credibility to their websites. – Wikipedia.
How to Choose the Right Certificate Authority
Certificate Authorities are like private security companies. They are the ones who issue digital certificates that facilitate the SSL establishment process. They also belong to a limited list of businesses that meet detailed criteria to maintain their place on that list. CAs who maintain their place on that list can issue SSL Certificates – so the list is exclusive.
The process is not quite as simple as it sounds, since before a certificate can be issued, the CA must check the identity of the website applying for it. The level of detail in those checks depend on what type of SSL is being applied for.
The best CA is one who has been in the business for some time and follows best practices in business, not only for itself but also for any partners associated with the business. Ideally, they should also be able to demonstrate proven expertise in the field.
Look for a CA that stays up to current standards, are actively involved in the security industry and has as many resources as possible that support their customers.
A good CA would also;
- Have reasonably short validation times
- Be easily accessible to its customers
- Have great support

