“This new Petya ransomware variant is like WannaCry without the kill switch, spreading automatically from computer to computer by itself and locking files,” Steve Malone, the director of security product management at Mimecast
Many organizations in Europe and the US have been crippled by a ransomware attack dubbed “Petya/NotPetya”. The malicious software has spread through large firms, It’s the second major global ransomware attack in the last two months. In early May, Britain’s National Health Service (NHS) was among the organizations infected by WannaCry, which used a vulnerability first revealed to the public as part of a leaked stash of NSA-related documents released online in April by a hacker group calling itself the Shadow Brokers. The WannaCry or WannaCrypt ransomware attack affected more than 230,000 computers in over 150 countries,
Initially, it was believed that this new ransomware was a new version of an older threat called Petya, but it was later discovered that this was a new strain altogether, which borrowed some code from the original Petya, hence the reason for calling it NotPetya, Petna, or SortaPetya.
The original Petya was a criminal enterprise for making money. This Petya/NotPetya is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware.
Like WannaCry, Petya/NotPetya/Petna/SortaPetya spreads rapidly through networks that use Microsoft Windows, this said, we feel it is important to answer some questions about; what is it, why is it happening and how can it be stopped?
What is ransomware?
Ransomware is a type of malware that blocks access to a computer or its data and demands money to release it.
 How does ransomware work?
How does ransomware work?
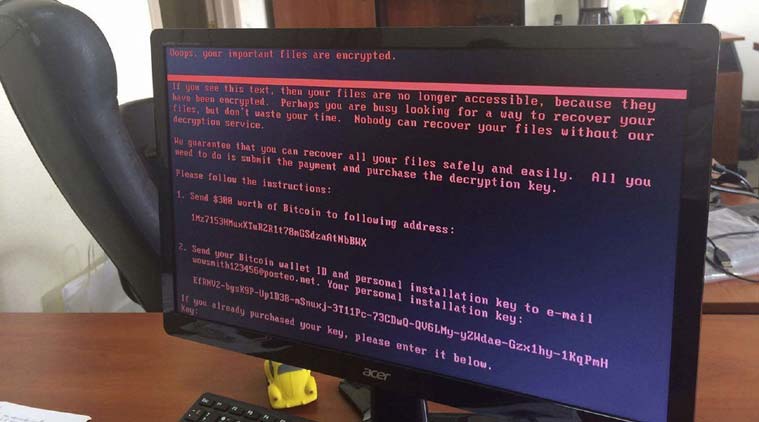
When a computer is infected, the ransomware reboots your computer and encrypts important documents and files and then demands a ransom, typically in Bitcoin, for a digital key(password) needed to unlock the files. If the victims do not have a recent back-up of the files they must either pay the ransom or face losing all of their files.
Crucially, NotPetya seeks to gain administrator access on a machine and then leverages that power to commandeer other computers on the network: it takes advantage of the fact that far too many organizations employ flat networks in which an administrator on one endpoint can control other machines
With admin access, the Petya/NotPetya software can not only lift credentials out of the RAM to access other internal systems, it can rewrite the local workstation’s hard drive’s MBR so that only Petya/NotPetya starts up when the machine reboots, rather than Windows, allowing it to display the ransom note; it can also encrypt the filesystem tables and files on the drive. NotPetya uses AES-128 to scramble people’s data. Needless to say, don’t pay the ransom – there’s no way to get the keys to restore your documents.
What should you do if you are affected by the ransomware?
The ransomware (Petya/NotPetya) infects computers and then waits for about an hour before rebooting the machine. While the machine is rebooting, you can switch the computer off to prevent the files from being encrypted and try and rescue the files from the machine, as flagged by @HackerFantastic on Twitter
If the system reboots with the ransom note, don’t pay the ransom – the “customer service” email address has been shut down so there’s no way to get the decryption key to unlock your files anyway. Disconnect your PC from the internet, reformat the hard drive and reinstall your files from a backup. Back up your files regularly and keep your anti-virus software up to date.
A perfc solution
For those concerned about the attack, there appears to be a fix, albeit one with limited effectiveness. By creating a read-only file – named perfc – and placing it within a computer’s “C:\Windows” folder, the attack will be stopped in its tracks. An explanation of how to do this has been posted by security news website Bleeping Computer and has been backed up by several other security experts. according to the BBC website;
However, while this method is effective, it only protects the individual computer the perfc file is placed on, though it will still act as a platform to spread the ransomware to other machines on the same network. As it stands, the attack of the Petya/NotPetya ransomware is likely to be much slower than last month’s WannaCry attack, code analysis has revealed that the Petya/NotPetya attack did not attempt to spread itself beyond the network it was placed on. Because of this, several experts are predicting that the attack will not spread significantly further than it did unless it is modified.
Researchers have so far been unable to locate a kill switch that would disable the ransomware attack entirely like they did for WannaCry.
In the meantime, like WannaCry, Petya/NotPetya is targeting a vulnerability in older Windows systems called EternalBlue. One of the best things you can do to protect yourself from these attacks is to download the patches Microsoft provides during updates. Microsoft released a patch to protect against the vulnerability on its Windows XP system in March. Earlier this month, it issued more patches for older Windows operating systems, citing the “elevated risk for destructive cyber attacks.”
If you enable Microsoft to automatically update your computer, you should have the patch. For older versions of Windows that Microsoft doesn’t generally support, you can go to the Microsoft website and download the patches you need to protect your computers based on the version of Windows you have.
In addition to the above, here are a few guidelines to protect you from the adverse effects of being infected by the Petya/NotPetya ransomware;
Backup you computer
You should always back up your computer just in case a ransomware attacks your computer so you have copies of your files in another location, like an external hard drive or in the cloud.
Don’t click on anything suspicious
Some of these attacks occur because of phishing emails. These emails are designed to make you think they are legitimate, but install malware on your computer once you open them.
Install protection programs
You should download protection programs that not only fight attacks but also notify you when there is a threat to your computer. These programs include firewalls, anti-virus programs, and other protective software. They can alert you if a malware is trying to encrypt your files and what they are doing to stop it.